How To Install Nmap In Termux
Introduction
Network Mapper (Nmap) is a free, open-source network security scanning tool. Past sending IP packets and analyzing the responses, Nmap can discover information about hosts and services on remote calculator networks.
Nmap tin besides audit the security of a device, identify the vulnerabilities of your network, or perform an inventory check with relative ease.
This tutorial shows how to install Nmap on Linux and explains Nmap'due south most important features.

Prerequisites
- A user with sudo privileges
- Access to a command line
Installing Nmap on Linux
The installation procedure of NMAP is simple and straightforward, requiring only a single command.
How to Install Nmap on Debian / Ubuntu
ane. Install Nmap on Ubuntu by entering the following command:
sudo apt-get install nmap 2. The organization prompts you to confirm the installation by typing y.
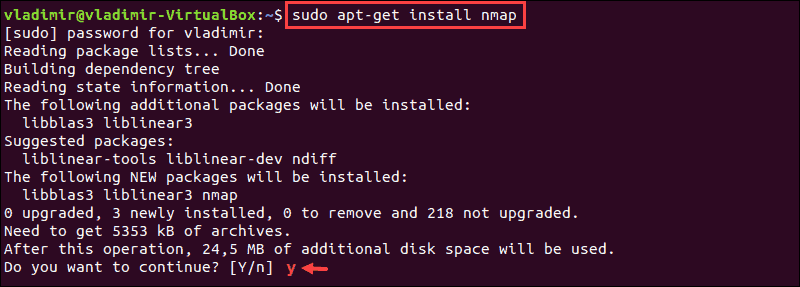
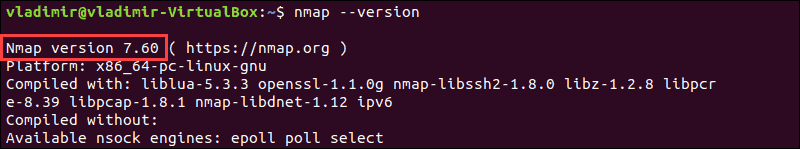
3. After the installation is finished, verify the installed version of Nmap past entering:
nmap –version In this case, the version is vii.60.
How to Install Nmap on CentOS / RHEL
1. To install Nmap on an RHEL based Linux distribution type the following command:
sudo yum install nmap This is an instance of the output in CentOS 7.
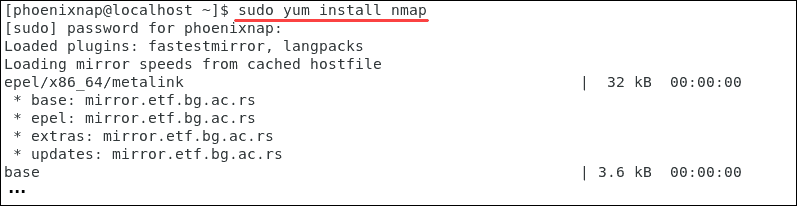
2. Confirm the installation past typing y.
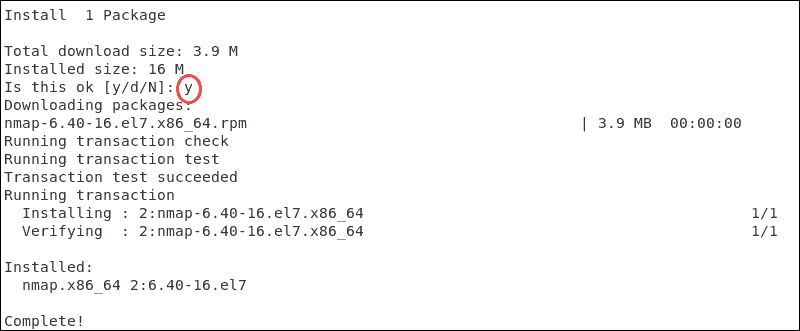
three. Like in other Linux distributions, once the installation is completed, check the version of Nmap by entering:
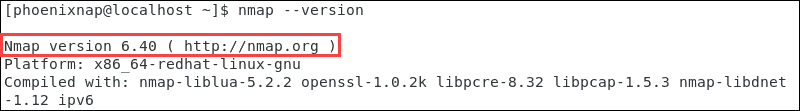
nmap –version In this instance, the installed version for CentOS 7 is six.40.
How to apply NMAP Security Scanner on Linux
Once you consummate the installation procedure, Nmap commands are identical regardless of the Linux distribution. Nmap provides a list of scanned targets along with supplemental information, based on the options and arguments used.
The article covers the basic options this tool has to offering. For a full list of options visit the Nmap official page or access the manual from your control line:
man nmap Note: It is important to emphasize that aggressive port scanning to find open up ports without permission tin be interpreted as malicious past third-political party organizations.
Scan IP range or subnet
To obtain general information of a remote system type:
sudo nmap target_IP or domain.com Instead of scanning private IPs, scan a whole IP range by defining it in your command line:
sudo nmap 185.52.53.2-222 The following command scans the entire specified subnet:
sudo nmap 185.52.53.0/24 Port Scanning with Nmap
Nmap is an efficient port scanner that recognizes half dozen port states:
- open – actively accepting TCP connections, UDP datagrams or SCTP associations
- airtight – attainable; still, no application is listening on the port
- filtered – nmap cannot determine whether the port is open due to packet filtering
- unfiltered – the port is attainable; nonetheless, nmap is unable to determine if it is open or airtight
- open|filtered – nmap cannot determine if a port is open or filtered
- closed|filtered – nmap cannot constitute if a port is airtight or filtered
Port Specification and Scan Order
By default, Nmap scans the thousand almost common ports for each protocol. It also offers options for specifying which ports are to exist scanned, and whether the scan is random or ordered.
The -p option allows y'all to specify port ranges and sequences:
sudo nmap –p 80,443 185.52.53.222 This command scans ports 80 and 443 for the defined host.
TCP SYN scan
Initiate TCP SYN for a fast and unobtrusive browse. Since this blazon of scan never completes TCP connections, information technology is often referred to as one-half-open scanning.
To run a TCP SYN scan, use the control:
sudo nmap -sS 185.52.53.222 Nmap: Scan Speed, Aggression, and Verbosity
Scan Speed
Scanning a big number of hosts is a time-consuming process. Nmap has an pick to ascertain the speed and thoroughness of the scan. Understandably, scans that need to avoid IDS alerts are slower.
Scan speeds designations beginning at T0 and span to T5. The higher the speed of the scan the more ambitious it is deemed.
Scan Output
The results of sophisticated tests and algorithms need to be presented in an understandable and structured manner to be useful. The –v command increases verbosity and forces Nmap to print more than information about the scan in progress.
Open up ports are shown in real-fourth dimension and completion time estimates are provided.
Aggressive Browse
The -A pick enables a comprehensive set of browse options. It enables:
- Os (Operating Arrangement) detection, too available with the -O command
- version scanning, also available with the -sV command
- script scanning, also bachelor with the -sC command
- traceroute, also available with the –traceroute command
Since Nmap accepts multiple host specifications on the control line, they do not need to be of the same type.
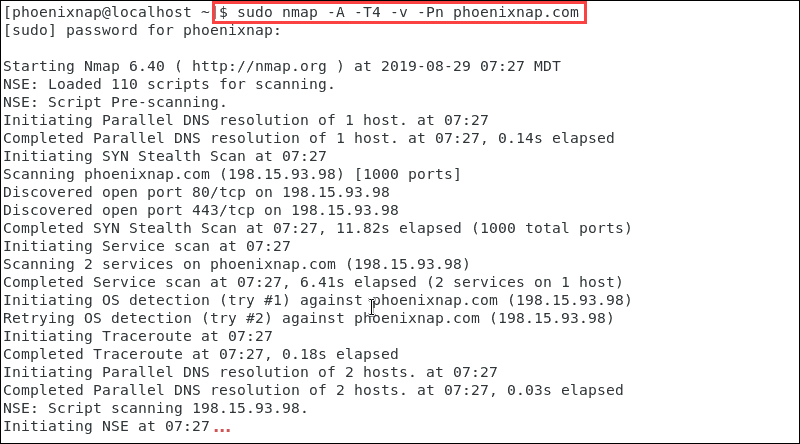
We tin combine the options listed to detect the Os and version, script scanning, and traceroute. Nosotros can besides use –A and –T4 for faster execution. Additionally, the –Pn selection to tell the Nmap tool not to initiate a ping scan:
sudo nmap –A –T4 –five –Pn phoenixnap.com The output compiles and presents the information from the scan we requested.
Conclusion
Now you know how to install and employ Nmap on your Linux system. Nmap has many bachelor options and tin can be a powerful and versatile scanning tool to discover network vulnerabilities.
Acquire 17 more than Nmap Commands with examples in this article!
Was this article helpful?
Yep No
Source: https://phoenixnap.com/kb/how-to-install-use-nmap-scanning-linux
Posted by: mcgowanmangst.blogspot.com


0 Response to "How To Install Nmap In Termux"
Post a Comment